Why Cyber Forensic Investigation Matters in Today's Digital World
What is cyber forensic investigation? It's the scientific process of identifying, preserving, analyzing, and presenting digital evidence from computers and networks in a legally admissible manner. This digital detective work combines computer science, legal expertise, and investigative skill to solve crimes that happen in cyberspace.
The stakes have never been higher. In 2022, the FBI estimated that computer crimes cost Americans $10.3 billion in annual losses. Every data breach and digital fraud leaves behind a trail of digital footprints. The question isn't whether these crimes will happen—it's whether organizations have trained professionals who can trace those footprints back to the source. From recovering deleted evidence of fraud to tracing a phishing email, cyber forensic investigators are critical in the pursuit of justice.
This guide walks you through what cyber forensic investigation is, how it works, the tools used, the challenges faced, and how you can build a career in this growing field.
I'm Joshua McAfee, and I've dedicated my career to training professionals who protect, prevent, and pursue justice. Understanding this field is essential for anyone in law enforcement, intelligence, or corporate security who wants to build a meaningful, future-proof career.

What is a Cyber Forensic Investigation? The Art of Digital Detective Work
Imagine a crime scene where evidence can vanish in milliseconds and a single mishandled byte can render findings inadmissible in court. That's the reality of what is cyber forensic investigation—it's detective work for the digital age.
At its heart, a cyber forensic investigation applies investigative techniques to digital environments to uncover facts, identify perpetrators, and understand the impact of cyber incidents. The discipline focuses on gathering digital evidence that can withstand scrutiny in legal proceedings, whether for a criminal court, civil dispute, or internal corporate investigation. The goal is to reconstruct events and attribute actions to bring clarity to complex digital mysteries. For background on how the field emerged, see this overview of the history of computer forensics.
Cyber Forensics vs. Digital Forensics: Understanding the Scope
While often used interchangeably, "cyber forensics" and "digital forensics" have a key difference.
Digital forensics is the broad umbrella term for recovering and investigating material from any digital device, like a computer, mobile phone, or smart watch.
Cyber forensics is a specialization that focuses on networked environments and internet-related incidents. This includes hacking attempts, data breaches, and online fraud where networks are central to the crime. In short, all cyber forensics is digital forensics, but not all digital forensics is cyber-related. For a neutral primer, the Digital forensics entry provides a concise overview of the broader discipline.
Primary Objectives of a Cyber Forensic Investigation
A cyber forensic investigation has several critical objectives:
- Identify attackers and their methods to understand who was responsible and what vulnerabilities were exploited.
- Assess the damage and scope of the incident to determine what data was accessed or stolen.
- Collect admissible evidence in a forensically sound manner to ensure its integrity and authenticity for court.
- Support legal action, whether for criminal charges or civil litigation.
- Reconstruct a sequence of events to create a clear timeline of what happened.
- Improve defenses by providing insights to prevent future incidents.
The end result is a comprehensive report, and knowing how to write an investigation report is a critical skill.
Cyber Forensics vs. Traditional Auditing
Cyber forensics is not the same as a traditional audit. Their objectives, scope, and methodologies are worlds apart.
| Feature | Cyber Forensics Investigation | Traditional Auditing Process |
|---|---|---|
| Objective | To uncover evidence of a crime or incident for legal or internal action. | To verify compliance with policies, regulations, or financial accuracy. |
| Scope | Focused on specific incidents, seeking anomalies and malicious activity. | Broad, routine examination of systems and records for accuracy. |
| Timing | Reactive and urgent, initiated in response to a suspected incident. | Proactive and periodic, typically scheduled annually or quarterly. |
| Methodology | Highly technical, involving deep dives into raw data, logs, and network traffic with specialized forensic tools. | Relies on sampling, interviews, and documentation review to check controls. |
| Legal Basis | Requires specific authorization and strict chain of custody for legal admissibility. | Governed by internal policies; data access is typically routine. |
| Outcome | Evidence for legal proceedings, disciplinary actions, or incident response. | A report on compliance status and recommendations for improvement. |
Cyber forensics is investigative work to build a case, while auditing is compliance work to check if rules are being followed. When something goes wrong, you call a forensic investigator. To ensure systems run as planned, you schedule an audit.
The Cyber Forensic Investigation Process: From Seizure to Courtroom
A solid investigation follows a structured, scientific method to ensure that findings hold up under scrutiny. Mishandling evidence or breaking the chain of custody can invalidate an entire case. The process is typically organized into five key phases: Identification, Preservation, Analysis, Documentation, and Presentation.
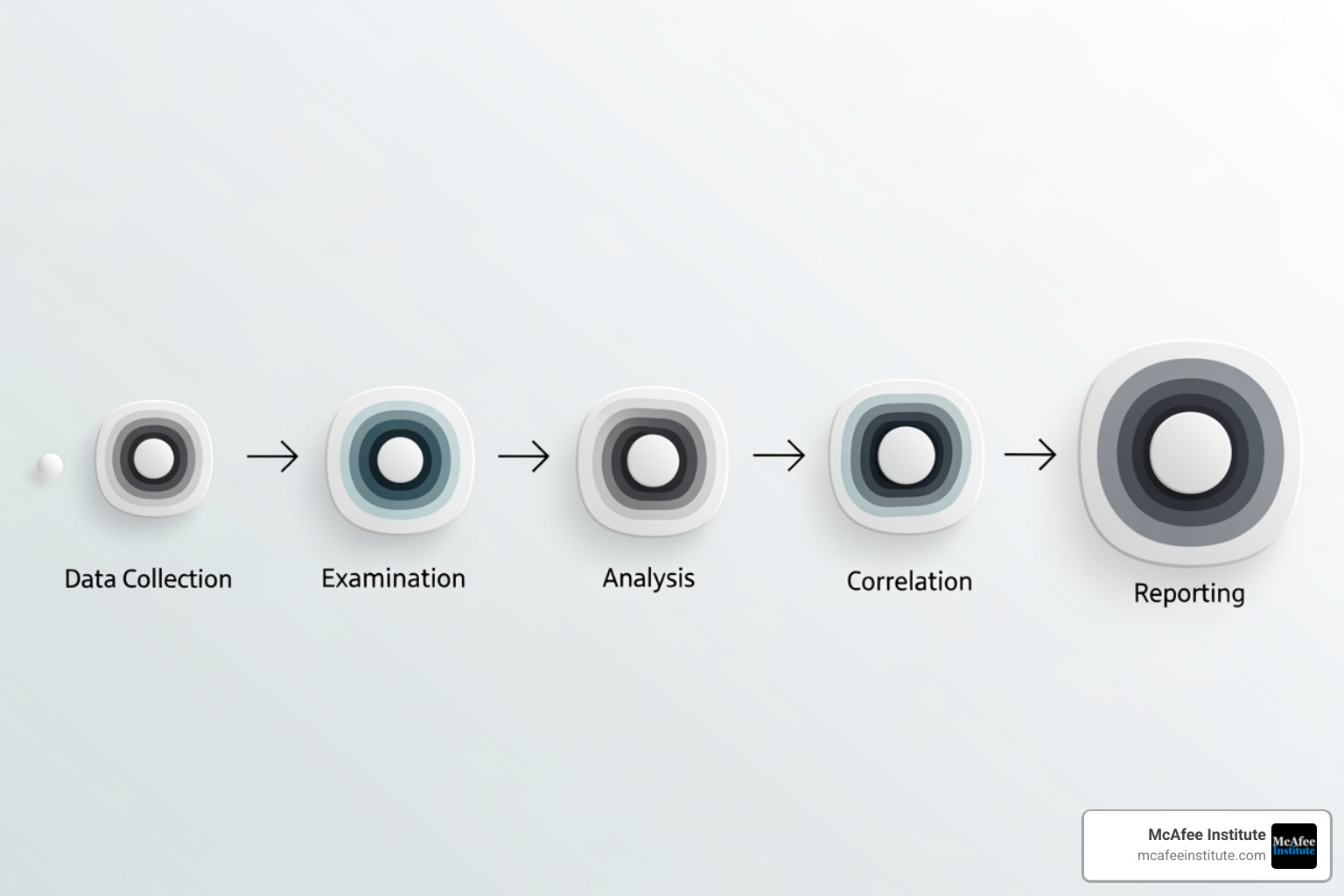
Phase 1 & 2: Identification and Preservation
These initial phases are about securing the digital crime scene. Identification involves locating potential sources of evidence, such as computers, servers, mobile devices, and network logs.
Preservation is critical because digital evidence is fragile. It involves capturing data without altering it. Investigators must handle two types of data:
- Volatile data (e.g., RAM, active network connections) disappears when a device loses power and must be captured from a live system.
- Persistent data (e.g., files on a hard drive) remains after power loss.
To protect original evidence, investigators use write-blockers to prevent modifications and create a forensic image—a bit-for-bit copy of the storage media. Analysis is always performed on this copy. To verify the copy's integrity, hashing algorithms (like SHA-1) are used to create a unique digital fingerprint for the original data and the copy. If the hashes match, the copy is identical. A strict chain of custody is maintained throughout.
What is cyber forensic investigation analysis?
This is where raw data is transformed into answers. Key techniques include:
- Data recovery and file carving: Recovering deleted files and fragments from unallocated disk space.
- Keyword searching: Scanning large datasets for relevant terms, phrases, or patterns.
- Timeline analysis: Reconstructing the sequence of events by correlating timestamps from files, logs, and browser history.
- Steganography detection: Uncovering data hidden within other files, like images or audio.
- Data correlation: Cross-referencing information from multiple sources (e.g., network logs and system events) to build a complete picture.
Open-Source Intelligence (OSINT) is also valuable for gathering context on threat actors from public sources.
Phase 4 & 5: Documentation and Presentation
Brilliant analysis is useless if not documented and communicated effectively.
Documentation is a continuous process. Investigators maintain detailed notes, log all actions, and carefully track the chain of custody for all evidence. This creates a verifiable audit trail that can withstand legal scrutiny.
Presentation involves translating technical findings into actionable insights for audiences like juries, executives, or law enforcement. This is typically done through a formal report that outlines the methodology, evidence, and conclusions in clear, objective language. For legal cases, findings must be admissible in court, and investigators may be called to provide expert testimony, explaining complex concepts in understandable terms.
The Investigator's Toolkit: Technologies, Challenges, and Specializations
A successful cyber forensic investigation relies on a combination of skilled professionals and purpose-built technology. While thorough investigations can be a significant investment, they are crucial for protecting an organization's reputation, data, and legal standing.
Key Tools and Technologies
An investigator's toolkit is constantly evolving, but several categories of tools are foundational:
- Forensic Imaging Tools: Create exact, bit-for-bit copies of storage media (e.g., hard drives) without altering the original evidence. Open-source tools like Autopsy and The Sleuth Kit are widely used.
- Data Analysis Platforms: Process massive volumes of digital evidence, enabling file carving, keyword searching, and timeline reconstruction.
- Network Traffic Analyzers: Tools like Wireshark capture and decode network packets to reveal communication patterns and suspicious activity.
- Memory Forensics Tools: The Volatility Framework and similar tools examine volatile data from a computer's RAM to find running processes and active network connections.
- Mobile Device Forensics Tools: Specialized applications that extract data like text messages, call logs, and location data from smartphones and tablets.
- Evidence Preservation Hardware: Write-blockers are essential devices that prevent any modification to original evidence during the imaging process.
What are the challenges of a cyber forensic investigation?
Investigators face several persistent challenges that require advanced skills and training:
- Encryption and Anti-Forensics: Attackers use encryption to hide data and anti-forensic techniques to erase or obscure their digital footprints.
- Volume of Data: Modern systems contain petabytes of data, making it difficult to find the "needle in a digital haystack."
- Cloud Environments: Investigations in the cloud are complicated by shared infrastructure, multi-tenancy, and reliance on third-party providers for data access.
- Jurisdictional Boundaries: Cybercrimes often cross international borders, creating complex legal and logistical problems for evidence collection.
- Volatile Data Preservation: Critical evidence in RAM is lost forever if a system is powered down before it can be captured.
- Evolving Technology: Investigators must constantly learn about new devices, operating systems, and attack methods. How AI is transforming investigations is one area helping to address some of these challenges.
Types of Cyber Forensics Specializations
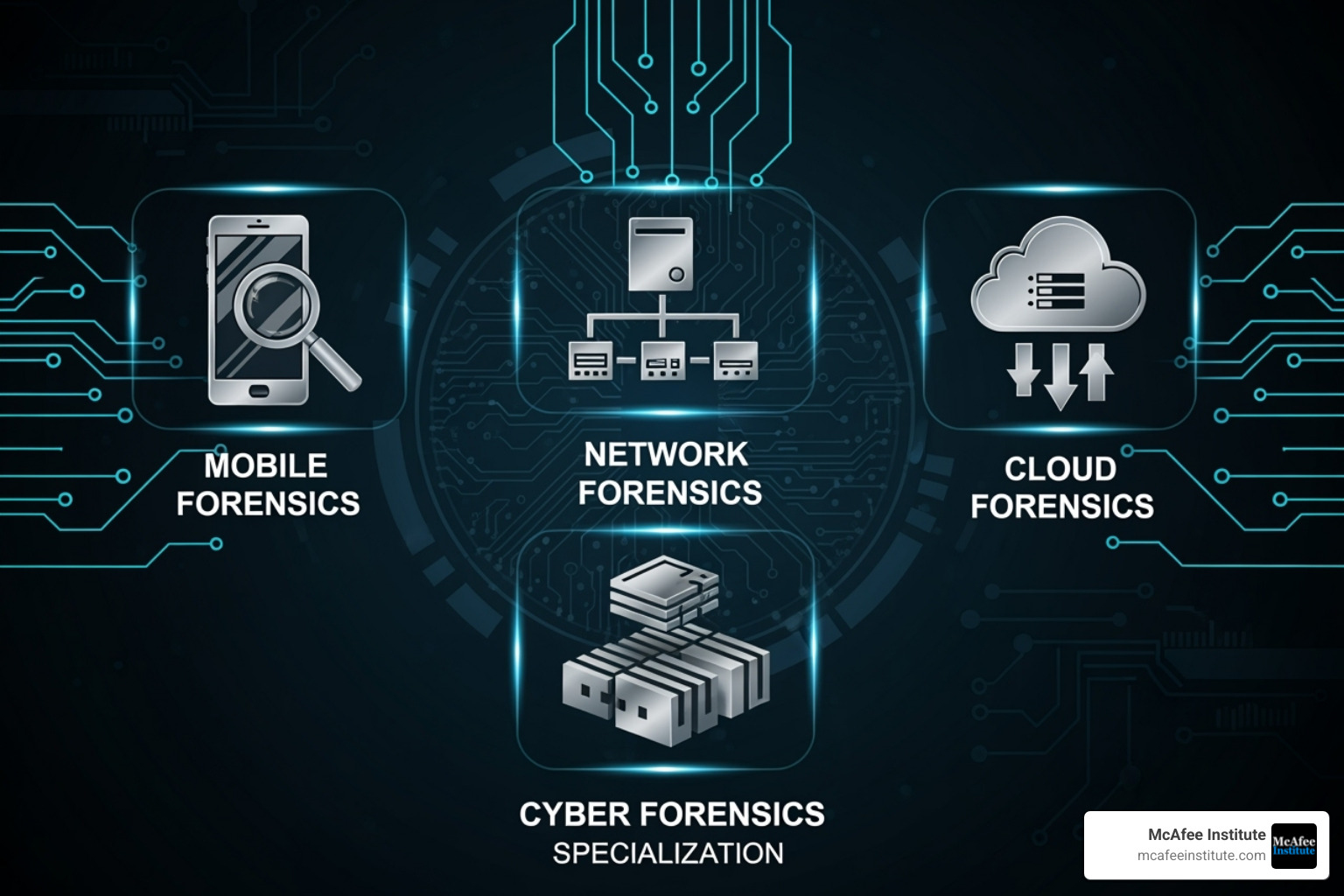
The field has evolved into several specialized branches:
- Network Forensics: Analyzing network traffic to identify intrusions and trace attacker movements.
- Mobile Device Forensics: Extracting critical data from smartphones and tablets.
- Cloud Forensics: Navigating the unique technical and legal challenges of investigating incidents in cloud environments.
- Malware Forensics: Dissecting malicious software to understand its function, origin, and impact.
- Database Forensics: Examining databases to detect fraud, data manipulation, or insider threats.
- Cryptocurrency Forensics: Tracing transactions on blockchain networks to investigate financial crimes. Professionals can Become a Certified Cryptocurrency Forensic Investigator (CCFI) to master these skills.
Building a Career in Cyber Forensics
The demand for skilled cyber forensics professionals is stronger than ever, with the global cost of cybercrime expected to reach $10.5 trillion annually by 2025. This field offers a dynamic career path with significant impact, strong earning potential, and opportunities in both law enforcement and the corporate sector. As organizations face more sophisticated threats, they need investigators who can uncover the truth hidden in digital evidence.
Essential Skills for a Cyber Forensic Professional
To excel in this field, you need a blend of technical, analytical, and soft skills:
- Analytical Thinking: The ability to dissect complex problems, identify patterns in data, and draw logical conclusions.
- Technical Proficiency: A deep understanding of operating systems, network protocols, file systems, and hardware.
- Legal Knowledge: Understanding of relevant laws, regulations, and evidentiary rules like chain of custody to ensure findings are legally sound.
- Communication Skills: The ability to clearly articulate complex technical findings to non-technical audiences, both verbally and in written reports.
- Attention to Detail: Meticulousness is crucial, as a single overlooked detail can make or break a case.
- Ethical Conduct: Upholding the highest ethical standards is paramount when handling sensitive information.
How to Start Your Career Path
A clear path exists for aspiring professionals:
- Education: A degree in a related field like computer science, IT, or digital forensics provides a strong foundation.
- Professional Certifications: Validate your skills with industry-recognized credentials. McAfee Institute offers government-recognized certifications like the Certified Expert in Cyber Investigations (CECI). These prove you have mastered the skills employers seek. OSINT certifications are also essential for investigators.
- Hands-on Practice: Practical experience is invaluable. Use online labs and simulations to build and hone your skills in realistic scenarios.
- Networking: Join professional industry groups to connect with peers, learn about emerging trends, and find job opportunities.
- Building a Portfolio: Create mock reports and document your lab work to showcase your skills to potential employers.
McAfee Institute is dedicated to empowering professionals with programs that offer lifetime access, live instructor support, and free updates for life. Our training translates directly into career advancement and leadership opportunities.
Frequently Asked Questions about Cyber Forensic Investigation
What is the main difference between cyber forensics and digital forensics?
Digital forensics is the broad field of recovering evidence from any digital device. Cyber forensics, on the other hand, is a specialized branch of digital forensics that focuses specifically on crimes involving networked environments and the internet, such as data breaches, hacking incidents, and online fraud. In short, all cyber forensics is digital forensics, but not all digital forensics is cyber-related.
Is cyber forensics a good career choice?
Yes, it is an excellent career choice. The demand is high, with the global cost of cybercrime projected to hit $10.5 trillion annually by 2025. The work offers a genuine impact in both law enforcement and corporate sectors, strong job security, and competitive salaries. If you enjoy technical problem-solving and want a career that makes a difference, cyber forensics is a rewarding path.
What kind of evidence is collected in a cyber forensic investigation?
Investigators collect a wide range of digital evidence from any device or service that can store data. This includes:
- Persistent Data: Files stored on hard drives, SSDs, and USB drives, including documents, images, and even deleted files.
- Volatile Data: Information that exists only while a system is powered on, such as data in RAM and active network connections.
- System and Network Logs: Records of user logins, file access, application usage, and network activity from firewalls and other devices.
- Communications: Emails, instant messages, and social media interactions.
- Browser History: Records of websites visited, searches performed, and files downloaded.
- Metadata: Data about data, such as file creation/modification dates and author information, which is crucial for building timelines.
Conclusion: Advance Your Career in Digital Investigations
We've explored what is cyber forensic investigation: the art of uncovering truth from digital evidence. From its meticulous five-phase process to the specialized tools and skills required, this discipline is indispensable in an age where cybercrime costs are projected to hit $10.5 trillion annually by 2025. The need for skilled digital detectives is exploding.
This career is about more than job security; it's about making a tangible difference by protecting assets, pursuing justice, and preventing future attacks. However, success in this field demands rigorous methodology and expertise that can only come from structured, comprehensive training.
At McAfee Institute, our programs are built for professionals serious about building a career that matters. Our government-recognized certifications are designed by experts with real-world law enforcement and intelligence experience. We offer lifetime access, live instructor support, and free updates for life—no annual renewals or hidden fees.
The future of digital investigations needs you. To build a high-impact career, explore government-recognized programs like the Certified Expert in Cyber Investigations (CECI) from McAfee Institute.











Share:
Blockchain Breadcrumbs: Mastering the Art of Crypto Tracing
From Wallet to Wallet: A Forensic Guide to Monitoring Crypto Transactions