Why Crypto Trace is Essential for Modern Financial Investigations
Crypto trace is the process of tracking cryptocurrency transactions across blockchain networks to identify illicit activity, locate stolen funds, and connect digital wallets to real-world identities. Contrary to the myth of complete anonymity, most cryptocurrencies are pseudonymous. This means every transaction is permanently recorded on a public ledger, creating a digital trail for investigators to follow.
Quick Answer: What You Need to Know About Crypto Trace
- What it is: A digital forensic technique that follows the movement of funds across blockchain networks.
- Why it matters: Law enforcement has frozen or recovered $34 billion in illicit funds using blockchain intelligence.
- How it works: By analyzing public transaction data, clustering wallet addresses, and linking them to real-world identities through exchanges.
- Key challenge: Criminals use mixers, privacy coins, and cross-chain transfers to obscure their tracks.
- Who uses it: Federal agencies, financial institutions, crypto exchanges, and specialized investigators.
The critical difference between anonymity and pseudonymity is that while your name isn't directly on a transaction, the wallet addresses, amounts, and timestamps are visible forever. This permanent public record is why even sophisticated criminals get caught; their digital footprints never disappear, creating an unprecedented opportunity for investigators who can read these digital breadcrumbs.
I'm Joshua McAfee, and in my career training thousands of investigators, I've seen crypto trace capabilities become non-negotiable for modern financial crime investigations. Understanding how to follow digital assets is now as fundamental as following a paper trail.
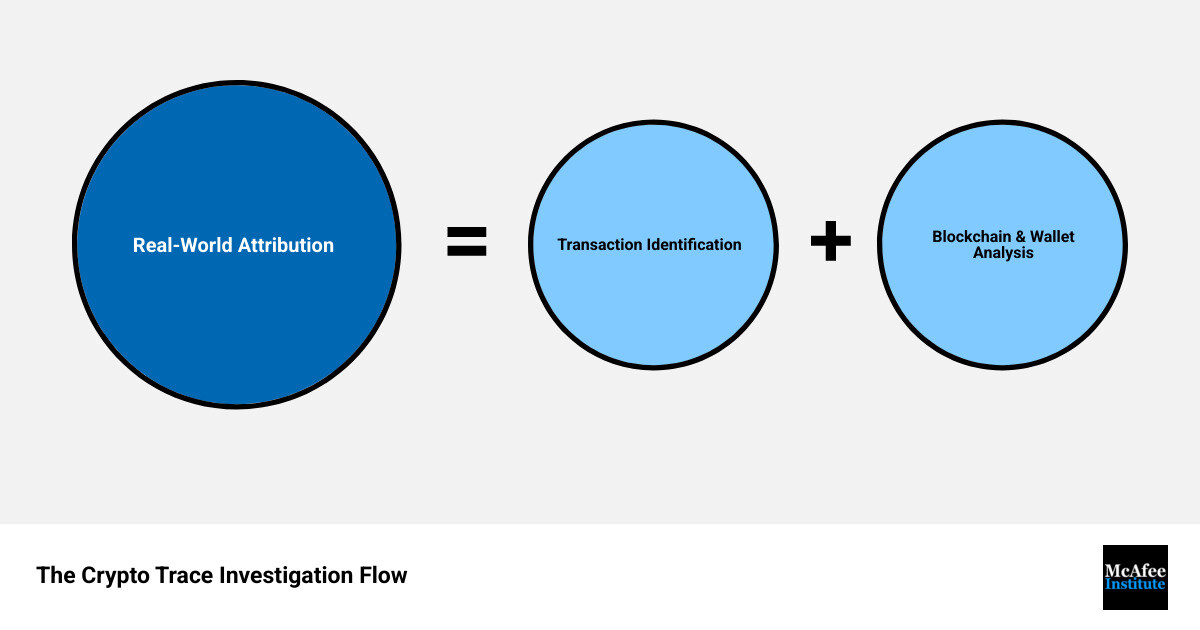
What is Cryptocurrency Tracing and Why is it Crucial for Investigators?
At its core, crypto trace is detective work for the digital age. It's a specialized digital forensic technique for following cryptocurrency as it moves across blockchain networks—tracking its origin, destination, and ultimately connecting digital wallets to real-world entities.
Think of it as following footprints in the snow, except these footprints never melt. Every transaction leaves a permanent mark that skilled investigators can analyze to map how illicit funds move through the digital economy.
This capability is crucial because criminals have acceptd cryptocurrency, and investigators must meet them on that battlefield. Crypto trace is essential for:
Combating Financial Crime: Ransomware gangs, investment scams, and money laundering operations often rely on the false belief that crypto is untraceable. Tracing allows investigators to identify perpetrators and dismantle their networks. The FBI's identification of cryptocurrency funds stolen by the DPRK is a prime example of tracing state-sponsored actors.
Asset Recovery: Stolen cryptocurrency doesn't just vanish. Tracing it is the first step toward recovery. Law enforcement agencies have successfully frozen or recovered an astounding $34 billion in illicit funds using blockchain intelligence, returning real money to victims.
Regulatory Compliance: Financial institutions and exchanges use crypto trace to comply with Anti-Money Laundering (AML) regulations. They can monitor for suspicious activity, flag illicit funds, and avoid facilitating crime. Over 45 global regulators now use blockchain intelligence to inform policy and protect consumers.
For law enforcement and defense agencies, tracing cryptocurrency is as fundamental as fingerprint analysis. It provides critical intelligence for investigating everything from fraud and darknet markets to terrorism financing.
Since most blockchain data is public, the principles of Open-Source Intelligence (OSINT) apply perfectly. The challenge isn't getting the data—it's knowing how to interpret it. Our guide on Understanding OSINT: A Comprehensive Guide explores these foundational techniques.
In short, crypto trace brings accountability to a world once thought to be outside traditional oversight. It turns the blockchain from a criminal's hiding place into a permanent record for investigators.
The Mechanics of the Blockchain: How Tracing is Possible
To understand how investigators track cryptocurrency, you must understand the technology itself. The blockchain is designed for transparency, not secrecy—a fact that is fundamental to any crypto trace investigation.

A blockchain is a public ledger—a permanent, unchangeable record of every transaction. When someone sends Bitcoin or Ethereum, the transaction is broadcast and recorded in a block. Once added to the chain, it cannot be deleted or modified. This immutability is what makes the blockchain a powerful forensic tool.
Each transaction contains key transaction data: the sender's and recipient's wallet addresses, the amount, and a timestamp. While wallet addresses are pseudonymous strings of characters, they create a detailed map of financial movement. Think of blockchain transactions not as sealed envelopes, but as public postcards that everyone can read.
Bitcoin's system of Unspent Transaction Outputs (UTXOs) is particularly useful for investigators. When you spend Bitcoin, you use previous UTXOs as inputs, and any leftover amount is sent back to you as a new UTXO, like getting change. This creates a clear, unbroken chain of custody for every fraction of a coin, allowing us to trace funds as they move from address to address.
This system enables a powerful technique called the common-input-ownership heuristic. The principle is simple: if a single transaction is funded by inputs from multiple different wallet addresses, it's almost certain that one person or entity controls all those addresses. This allows investigators to perform wallet clustering, grouping addresses that are likely controlled by the same entity and revealing the true scale of an operation.
Bitcoin's transparency is a defining feature. Ethereum operates with similar transparency, though its smart contracts add another layer of complexity and analytical opportunity. The blockchain records not just what happened, but the relationships and patterns between transactions.
Of course, a successful crypto trace requires more than technical knowledge. As we teach in How to Write an Investigation Report: A Step-by-Step Guide, clear documentation is crucial for presenting complex findings. The evidence always exists on the blockchain; the challenge is finding it, interpreting it, and connecting it to the real world.
The Core Techniques of a Crypto Trace Investigation
Conducting a crypto trace investigation is modern-day detective work. It involves following money through a complex landscape of blockchain networks and obfuscation techniques. This is where specialized knowledge and cutting-edge technology converge to solve convoluted financial schemes.
At its heart, crypto trace is on-chain analysis—examining the digital breadcrumbs left on the blockchain. The job is to collect these breadcrumbs, connect them, and follow them to their source. While the process is iterative, a systematic framework is key. As investigations grow more complex, emerging technologies can help manage the workload, a topic explored in How AI is Transforming the Future of Investigations.
How Does a Crypto Trace Work? The Step-by-Step Process
While every case is unique, the fundamental process of a crypto trace remains consistent:
Transaction Analysis: We start with the transaction of interest—a ransom payment, fraudulent transfer, etc. We examine every detail: wallet addresses, amount, timestamp, and even the transaction fee, which can reveal clues about the sender's urgency.
Wallet Clustering: Using techniques like the common-input-ownership heuristic, we identify multiple wallet addresses likely controlled by the same entity. This expands our view from a single wallet to a network of connected addresses.
Address Attribution: This is the ultimate goal: linking pseudonymous wallet addresses to real-world identities. We look for touchpoints with the traditional financial system, such as deposits to cryptocurrency exchanges that collect Know Your Customer (KYC) data. This information can definitively connect a wallet to a person.
Flow Tracking: We patiently follow the funds as they move, sometimes through dozens of wallets or across different blockchains. This maps the entire financial network and identifies key players. Research like Tracing Transactions Across Cryptocurrency Ledgers has advanced our ability to track funds even when criminals try to break the chain.
Reporting: Finally, we compile our findings into a comprehensive report. This presents the evidence in a way that is actionable for law enforcement, understandable for courts, and useful for compliance teams.
The Investigator's Toolkit: From Explorers to Intelligence Platforms
Our tools have evolved dramatically. While the investigator's judgment is irreplaceable, technology can accelerate the process.
Blockchain explorers (like public sites for Bitcoin or Ethereum) are the starting point. They are free search engines for blockchain data, allowing you to look up any transaction or wallet address. They are useful for simple cases but are inadequate for complex investigations.
This is where blockchain intelligence platforms come in. These commercial tools don't just show raw data—they analyze, contextualize, and visualize it. They use advanced algorithms to automatically cluster related addresses, saving countless hours of manual work. Their real power lies in vast databases of labeled addresses associated with exchanges, scams, sanctioned entities, and more. When funds flow to a wallet flagged as a known ransomware group, that's immediately actionable intelligence.
These platforms offer powerful graph analysis tools that visualize transaction networks, making it easier to spot hubs and understand criminal structures. They also handle cross-chain transactions, tracking funds as they hop between blockchains—a crucial capability, as criminals rarely stay on a single network.
Mastering these techniques requires specialized training. The Certified Digital Currency Investigator (CDCI) program provides hands-on experience with these tools and methodologies, separating amateur sleuthing from professional-grade analysis in this rapidly growing field.
Overcoming Obstacles: Challenges in Tracing Digital Assets
While blockchain transparency provides incredible investigative power, criminals are constantly developing new tactics to hide their tracks. Understanding these obstacles is just as important as knowing the tracing techniques themselves.

Common Obfuscation Techniques
Criminals use a sophisticated toolkit to complicate crypto trace investigations. The most common methods include:
Mixers and Tumblers: These services act like digital laundromats, pooling funds from many users to break the clear on-chain link between sender and recipient.
Chain Hopping: Criminals rapidly convert funds from one cryptocurrency to another (e.g., Bitcoin to Ethereum to Litecoin), adding layers of complexity to the trail.
Cross-Chain Transactions: Using interoperability protocols, criminals move funds seamlessly between different blockchains to make tracing more difficult.
Decentralized Finance (DeFi) Protocols: By routing funds through complex, non-custodial smart contracts for swapping or lending, criminals create a maze of transactions that is difficult to untangle.
Privacy-Focused Cryptocurrencies: Coins like Monero and Zcash are engineered for opacity, using cryptographic techniques to hide senders, recipients, and transaction amounts. When illicit funds are converted to these coins, it can create a dead end for investigators.
These techniques are always evolving, which is why staying current with the latest investigative methods is crucial. Resources like our guide on 5 Incredible OSINT Techniques to Supercharge Your Investigations in 2025 can help investigators adapt.
Challenges and Limitations in a Crypto Trace
Beyond criminal tactics, investigators face several systemic challenges:
Jurisdictional Issues: Cryptocurrency is borderless, but laws are not. Tracing funds across multiple countries means navigating different legal systems, which can cause significant delays in an investigation.
Evolving Legal Frameworks: The laws surrounding digital assets are still maturing. As noted in "Beyond Bitcoin: Issues in Regulating Blockchain Transactions," regulatory gaps create problems for cross-border cases involving asset seizure and data sharing.
Scale and Volume: Major blockchains process hundreds of thousands of transactions daily. Analyzing this massive volume of data, especially across multiple hops and chains, requires significant computational resources and expertise.
Attribution Difficulties: The critical step is linking pseudonymous wallets to real people, which often relies on data from centralized exchanges. If criminals operate exclusively through decentralized platforms or use privacy coins, attribution becomes exponentially harder.
Evolving Criminal Tactics: As tracing tools improve, criminals adapt. Effective crypto trace investigation requires a commitment to continuous education to stay ahead of the curve, which is a core focus of the Certified Digital Currency Investigator (CDCI) program.
These challenges are significant but not impossible. With the right training, tools, and approach, investigators can successfully steer the complexities of digital asset tracing.
Frequently Asked Questions about Crypto Tracing
We often encounter common questions about the capabilities and limitations of crypto trace. Here are answers to some of the most frequent inquiries.
Can stolen crypto actually be recovered through tracing?
Yes, and crypto trace is the essential first step. Tracing allows investigators to follow stolen funds across the blockchain to identify where they end up. Often, these funds land in centralized exchanges that require user identity verification (KYC).
Once the funds are located, law enforcement can take legal action to freeze accounts and seize the assets. The results are tangible: agencies worldwide have frozen or recovered $34 billion in illicit funds through blockchain intelligence.
However, success is not guaranteed. It depends on the speed of the investigation, the obfuscation tactics used by the criminals, and cooperation between international law enforcement and exchanges. While recovery is challenging, tracing dramatically increases the odds.
Is Bitcoin truly untraceable?
No, this is a persistent myth. Bitcoin is not untraceable; it is pseudonymous. Every transaction is permanently recorded on its public blockchain, creating an indelible trail for anyone to see.
The wallet addresses are not tied to names, but they can be tracked. The breakthrough occurs when funds touch a regulated service like an exchange, where the pseudonymous address can be linked to a real-world identity via KYC data and legal process.
The FBI's successful recovery of the Colonial Pipeline ransom payment, as reported by The New York Times, demonstrated that Bitcoin's public ledger makes it traceable. While complex, the idea of complete anonymity is incorrect.
What skills are needed for a crypto trace investigation?
A successful crypto trace investigator needs a blend of traditional investigative skills and specialized technical knowledge. Key competencies include:
- Analytical Skills: The ability to sift through vast amounts of data to find patterns and draw logical conclusions.
- Blockchain Technology Understanding: Grasping how different blockchains (e.g., Bitcoin's UTXO model vs. Ethereum's account model) function.
- Tool Proficiency: Hands-on skill with blockchain explorers and advanced intelligence platforms to interpret data and visualize fund flows.
- Financial Crime Knowledge: Understanding money laundering typologies, fraud schemes, and criminal behavior to anticipate their moves.
- Data Interpretation: The ability to transform raw data into clear visualizations and reports for non-technical audiences.
- Legal and Regulatory Awareness: Knowledge of AML/KYC regulations and legal frameworks to ensure evidence is admissible.
- Adaptability and Continuous Learning: A commitment to staying current with new technologies and criminal tactics.
Mastering these skills is the focus of specialized training programs like the Certified Digital Currency Investigator (CDCI) certification, which provides the practical knowledge needed for real-world success.
Conclusion: The Future of Digital Asset Forensics
Digital assets are now a fixture of the global financial system, and where money flows, crime often follows. This makes crypto trace an essential skill for anyone working to protect financial integrity. The myth of untraceable cryptocurrency has been debunked; the public nature of blockchains provides a powerful tool for investigators to follow digital footprints.
The future of digital asset forensics will be shaped by several key trends. As discussed in our article on How AI is Transforming the Future of Investigations, artificial intelligence will improve pattern detection. We also anticipate stronger international cooperation and clearer regulatory frameworks, addressing issues highlighted in publications like Beyond Bitcoin: Issues in Regulating Blockchain Transactions. Finally, cross-chain tracing capabilities will improve, building on research like Tracing Transactions Across Cryptocurrency Ledgers to make it harder for criminals to hide.
This remains a dynamic cat-and-mouse game. As our methods improve, criminals devise new obfuscation techniques, making continuous learning critical.
This is why we are passionate about specialized training at the McAfee Institute. The digital asset landscape changes fast, and investigators need education that keeps pace. Our Certified Digital Currency Investigator (CDCI) certification provides the practical skills you need to excel. With lifetime access, live instructor support, and free updates for life, you'll stay current as the field evolves—with no annual renewals or hidden fees.
The ability to conduct a thorough crypto trace is no longer optional. We invite you to become a Certified Digital Currency Investigator and position yourself at the forefront of this critical field.











Share:
Cyber Forensics Unpacked: Your Guide to Digital Evidence
Spotting Shadows Machine Learning's Edge in Cybersecurity