Why Digital Currency Investigation Is Now a Core Investigative Skill
Crypto tracing is the process of analyzing cryptocurrency transactions on public blockchains to identify fund movements, uncover illicit activity, and link digital wallets to real-world identities. Key components include:
- Transaction Analysis: Following the flow of funds.
- Wallet Clustering: Grouping addresses controlled by the same entity.
- Address Attribution: Linking addresses to people or organizations.
- Flow Tracking: Mapping the complete path of funds.
- Risk Scoring: Assessing exposure to illicit activity.
The myth of cryptocurrency anonymity is shattered. While many believe digital currencies are untraceable, every transaction creates a permanent, public record. In 2024 alone, $40.9 billion in illicit transactions funded everything from ransomware to terrorist financing.
Criminals leave digital breadcrumbs, and skilled investigators know how to follow them. The scale of this crime makes crypto tracing essential. Law enforcement has already recovered $34 billion in illicit funds using blockchain intelligence, with major successes like the seizure of $8.6 million from the Qakbot botnet and the FBI's identification of funds stolen by North Korea.
Traditional methods don't work on the blockchain. Investigators need specialized knowledge to analyze decentralized ledgers and attribute pseudonymous wallets to real people. Understanding crypto tracing is now as fundamental as tracing bank wires.
I'm Joshua McAfee, and I've seen how crypto tracing has become indispensable. At McAfee Institute, we provide specialized training to help investigators master these techniques and advance their careers in this critical field.
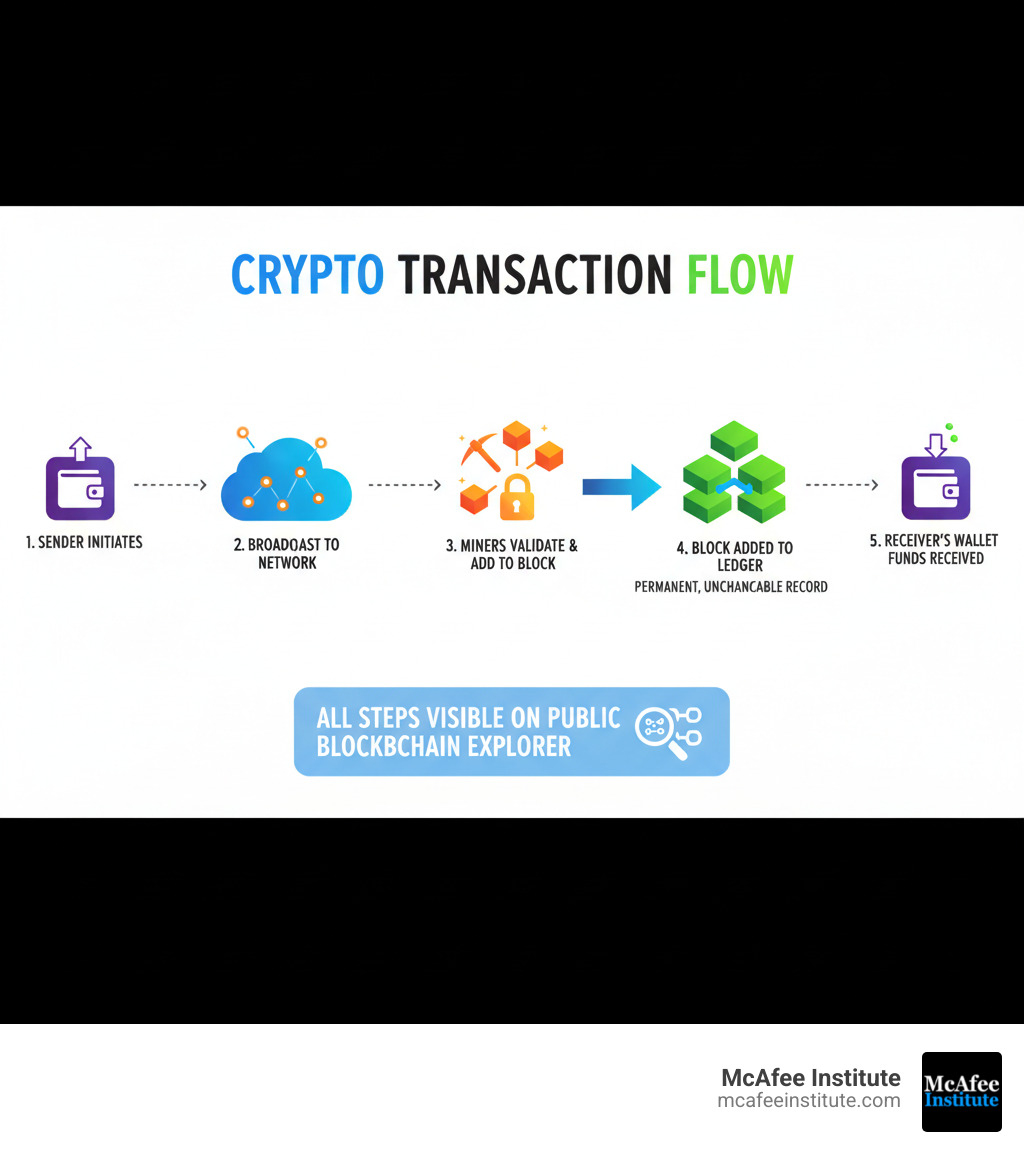
What is Crypto Tracing and Why is it Essential for Investigators?
Think of crypto tracing as following digital footprints. Most cryptocurrencies, like Bitcoin and Ethereum, operate on public blockchains where every transaction is recorded forever. These records are immutable, giving investigators a powerful advantage.
However, transactions are pseudonymous, not anonymous. They are linked to wallet addresses—long strings of characters—not real names. Pseudonymity means the trail exists; anonymity would mean it doesn't. The investigator's job is to connect those wallet addresses to real people and organizations, effectively following the money through the digital world to uncover criminal networks.

The Importance in Modern Investigations
With $40.9 billion in illicit transactions in 2024 alone, crypto tracing is no longer a niche skill. It's essential for:
- Combating Fraud: Criminals in investment, romance, and phishing scams increasingly demand crypto. Tracing these funds helps identify perpetrators and protect victims.
- Counter-Terrorism Financing: Defense agencies use crypto tracing to disrupt funding pipelines for terrorist organizations and prevent attacks.
- Ransomware Payments: Investigators have become adept at following ransom payments. The FBI's recovery of $8.6 million from the Qakbot botnet and the famous Colonial Pipeline case proved that crypto payments don't guarantee criminals anonymity. As The New York Times reported, this upended the idea that Bitcoin is untraceable.
- Asset Recovery: Beyond crime, tracing helps locate digital assets hidden in divorces or embezzled from companies. Globally, $34 billion in illicit funds have been recovered using blockchain intelligence.
- Securing Evidence: Immutable blockchain records provide robust, court-admissible evidence, as seen when the FBI identified cryptocurrency funds stolen by the DPRK.
Who Uses Crypto Tracing?
The need for crypto tracing expertise spans multiple sectors:
- Law Enforcement Agencies: From local police to the FBI and Interpol, agencies use tracing to investigate everything from drug trafficking to organized crime.
- Financial Regulators: Over 45 regulators worldwide use blockchain intelligence to enforce anti-money laundering (AML) rules and monitor compliance.
- Defense and National Security Agencies: These organizations track illicit funding for adversarial groups and counter state-sponsored hacking.
- Crypto Businesses: Exchanges and other Virtual Asset Service Providers use tracing for compliance, risk management, and fraud prevention.
- Corporate and Private Investigators: These professionals need tracing skills to investigate internal fraud, asset misappropriation, and recover stolen funds for clients.
- Intelligence Analysts: Tracing is a key component of Open-Source Intelligence (OSINT) for mapping criminal networks. Learn more in our Understanding OSINT: A Comprehensive Guide.
All these professionals must follow the money, and today, that money is on the blockchain.
The Investigator's Toolkit: Core Techniques for Crypto Tracing
Effective crypto tracing combines on-chain analysis (examining the public ledger) with off-chain analysis (connecting blockchain data to real-world information like exchange records or IP addresses). By correlating these sources and using heuristics—educated pattern recognition—investigators can break cases open.

Following the Digital Trail on the Blockchain
The investigation begins with the fundamentals of transaction analysis: examining sender/recipient addresses, amounts, and timestamps. From there, key techniques include:
- Wallet Clustering: Criminals use many addresses. Clustering groups them together by identifying shared spending patterns or common funding sources. This technique is validated by academic research, such as in "Tracing Transactions Across Cryptocurrency Ledgers".
- Flow Tracking: This involves mapping the complete journey of funds as they are split, merged, and moved through various intermediaries.
- Source and Destination Analysis: Identifying where funds came from (e.g., a hacked exchange, a ransomware address) and where they went (e.g., a centralized exchange to cash out, a darknet market) reveals the perpetrator's methods and intent.
Essential Tools and Technologies
Modern crypto tracing requires professional platforms. While blockchain explorers (Etherscan, Blockchain.com) are useful for basic lookups, serious investigations rely on more advanced tools.
Blockchain intelligence platforms like Chainalysis and TRM Labs are the industry standard. They analyze patterns, visualize fund flows, provide risk scoring, and trace activity across dozens of blockchains. These platforms transform raw data into actionable intelligence.
Graph analysis software, often built into these platforms, visualizes transactions as networks, making it easy to spot suspicious clusters and money laundering chains.
Open-Source Intelligence (OSINT) remains vital for linking addresses to people. Social media posts or public records can provide the crucial off-chain connection. Our guide on Five High-Value OSINT Techniques with AI Investigators Probably Haven't Thought Of (and How to Use Them Ethically) offers advanced strategies.
The Role of AI and Machine Learning
AI is amplifying the power of crypto tracing by automating complex analysis.
- Pattern Recognition: Machine learning algorithms can analyze millions of transactions to detect subtle illicit patterns, such as layering or peeling chains, that a human might miss.
- Predictive Risk Scoring: AI models assess the probability that a wallet is involved in illicit activity based on its transaction history and connections, allowing investigators to prioritize high-risk targets.
- Automating Analysis: AI handles tedious data gathering and preliminary analysis, freeing up investigators to focus on critical thinking and gathering off-chain intelligence.
AI doesn't replace investigators; it makes them faster and more effective. For more on this trend, see our article on How AI is Transforming the Future of Investigations.
Real-World Applications and Landmark Cases
The power of crypto tracing is best seen in its real-world results, which have led to the recovery of billions of dollars and the dismantling of major criminal operations.
Combating Illicit Finance and Recovering Assets
Law enforcement agencies have frozen or recovered an astounding $34 billion in illicit funds using blockchain intelligence. This success is built on landmark cases:
- In the Qakbot botnet case, meticulous crypto tracing led to the seizure of $8.6 million in ransomware funds.
- The Colonial Pipeline investigation famously saw the FBI recover a large portion of the ransom, proving that even Bitcoin transactions can be traced.
- The FBI's identification of funds stolen by the DPRK demonstrates how tracing serves critical national security interests.
These successes, along with countless solved investment and broker fraud cases, show that criminals can no longer hide behind pseudonymous wallets. Documenting these findings is crucial, and our guide on How to Write an Investigation Report: A Step-by-Step Guide can help create professional, court-ready reports.
Navigating Challenges: Privacy Coins and Obfuscation
Investigators face a constant battle against criminals' efforts to evade detection. Understanding these challenges is key to overcoming them.
Privacy-focused cryptocurrencies like Monero and Zcash are designed to obscure transaction details, making them much harder to trace than transparent currencies like Bitcoin.
| Feature | Transparent Cryptocurrencies (e.g., Bitcoin, Ethereum) | Privacy-Focused Cryptocurrencies (e.g., Monero, Zcash) |
|---|---|---|
| Transaction Visibility | All transactions, amounts, sender/receiver addresses are public. | Transaction details (sender, receiver, amount) are obscured using advanced cryptographic techniques. |
| Address Linkability | Addresses can often be clustered and linked to entities. | Addresses are typically one-time use or unlinkable, making clustering difficult. |
| Tracing Difficulty | Challenging but generally feasible with specialized tools. | Significantly more difficult, often requiring external intelligence or vulnerabilities. |
Criminals also use obfuscation techniques on transparent blockchains, including:
- Mixers and Tumblers: Services that pool and mix funds from many users to break the transaction trail.
- Cross-Chain Swaps: Moving funds between different blockchains (e.g., Bitcoin to Ethereum) to complicate tracking.
- DeFi Protocols: Using complex smart contracts, lending platforms, and liquidity pools to layer transactions and hide funds.
While these methods add complexity, they are not foolproof. Funds must eventually enter or exit through regulated entities like exchanges, which require Know Your Customer (KYC) verification. These on-ramps and off-ramps provide investigators with crucial opportunities to obtain records and identify suspects.
The Future of Crypto Investigations and How to Stay Ahead
The world of cryptocurrency is in constant flux, with criminals quick to exploit new technologies. For investigators, continuous learning is not just an advantage—it's a necessity to stay ahead in a field where tactics evolve daily.
The good news is that the investigative landscape is also maturing. Regulators worldwide are establishing clearer frameworks, increasing transparency requirements for exchanges and other Virtual Asset Service Providers (VASPs). At the same time, inter-agency collaboration between law enforcement, financial regulators, and intelligence services is reaching new levels of effectiveness.
This dynamic environment creates an urgent demand for professionals with specialized training in digital currency investigation.

Protecting Individuals and Organizations
While crypto tracing is a powerful recovery tool, prevention is always the best strategy.
- Practice Due Diligence: Thoroughly research any crypto project before investing. Be skeptical of guaranteed high returns.
- Secure Your Wallet: Use strong, unique passwords and enable two-factor authentication (2FA). For significant holdings, use a hardware wallet. Never share your private keys or seed phrase.
- Beware of Scams: Verify website URLs before entering credentials and be cautious of unsolicited investment offers, especially from people you've only met online. Romance or "pig butchering" scams are particularly devastating.
If you become a victim, report the crime immediately to the Internet Crime Complaint Center (IC3). The faster law enforcement has the information, the better the chance of tracing and recovering the funds.
Building Your Expertise in Digital Currency Investigation
For professionals in law enforcement, intelligence, and corporate security, crypto tracing is now a fundamental skill. The question isn't whether you need this expertise, but how you will acquire it.
At McAfee Institute, we've trained thousands of professionals globally and understand what it takes to succeed in real-world digital currency investigations. Our Certified Digital Currency Investigator (CDCI) program is built by investigators, for investigators.
You'll learn blockchain fundamentals, advanced tracing techniques, and how to use professional intelligence platforms. What sets our training apart is the lifetime access model: no annual renewals, no hidden fees, and free updates for life. You also get ongoing access to live instructor support from experts who have faced the same challenges you do.
Our government-recognized and employer-trusted certifications provide the credibility and skills to advance your career. The criminals are getting smarter, but with the right training, you can stay ahead.
Frequently Asked Questions about Crypto Tracing
Is it possible to get stolen cryptocurrency back?
Yes, recovery is possible, but it is complex. Unlike cash, cryptocurrency leaves a permanent, public record on the blockchain. Crypto tracing experts can follow this digital trail.
The process involves:
- Specialized Tracing: Investigators use advanced blockchain intelligence platforms to follow the funds through various intermediaries.
- Law Enforcement Involvement: Reporting the theft to agencies like the FBI provides access to legal authority and resources, including partnerships with tracing firms.
- Legal Action: Once funds are traced to an identifiable entity (like a crypto exchange), authorities can use court orders to freeze and seize the assets.
Success is not guaranteed, but the track record is strong. Law enforcement has recovered $34 billion in illicit funds using these methods, returning assets to thousands of victims.
How do investigators link a crypto wallet to a real person?
This is where digital analysis meets traditional detective work. Investigators connect pseudonymous wallets to real identities through several key methods:
- Know Your Customer (KYC) Data: Most legitimate crypto exchanges require users to provide ID. When funds are traced to an exchange, a subpoena can reveal the account holder's identity.
- Open-Source Intelligence (OSINT): Investigators find clues in public data. A social media post, forum comment, or online profile can sometimes link a person directly to a wallet address. Our Understanding OSINT: A Comprehensive Guide explores these techniques in greater depth.
- Transactional Patterns: Consistent transaction behavior can reveal habits, while interactions with already-identified wallets can create links.
- Collaboration with VASPs: Many crypto businesses (Virtual Asset Service Providers) actively cooperate with law enforcement to identify illicit activity.
What are the biggest challenges in crypto tracing?
Investigators face significant and evolving obstacles in crypto tracing.
- Privacy-Enhancing Technologies: Tools like mixers (which scramble funds) and privacy coins (Monero, Zcash) are designed to obscure the transaction trail, making tracing extremely difficult.
- Cross-Chain Transactions: Criminals move funds across different blockchains (e.g., from Bitcoin to Ethereum) to complicate tracking, requiring tools that can analyze multiple ledgers at once.
- Decentralized Platforms (DeFi): With no central company to subpoena, decentralized exchanges and protocols present a unique challenge to traditional investigative methods.
- Jurisdictional Complexities: Crime is global, but laws are local. Tracing funds across borders requires navigating a complex web of international laws and cooperation agreements.
- Volume and Evolving Tactics: The sheer volume of transactions requires AI-powered tools, and investigators must constantly adapt as criminals develop new obfuscation techniques.
These challenges highlight why continuous, specialized training is essential. Our Certified Digital Currency Investigator (CDCI) program is designed to keep you ahead of these evolving threats.











Share:
Criminal Profiling 101: Your Guide to Their Daily Grind
Cyber Forensics Unpacked: Your Guide to Digital Evidence