Why Social Media OSINT is Essential for Modern Investigations
Open source intelligence tools for social media are indispensable for today's investigators, analysts, and security professionals. The digital breadcrumbs left across social platforms hold critical answers for tracking suspects, uncovering influence networks, or verifying leads—if you know where to look.
Social Media Intelligence (SOCMINT), a subset of Open Source Intelligence, focuses on publicly available information from platforms like Facebook, Twitter, and LinkedIn. This user-generated content—posts, images, profiles, and interactions—creates a digital footprint that can reveal connections, locations, and intent.
In an era where criminal activity, threat actors, and disinformation campaigns operate online, investigators who don't leverage social media OSINT are at a significant disadvantage. The challenge isn't a lack of data but the overwhelming volume of it. Without the right tools and techniques, critical clues get buried in the noise.
This is where structured training and proven tools make a difference. Mastering open source intelligence tools for social media transforms investigators from reactive responders into proactive intelligence professionals, building real-world capabilities that solve cases and advance careers.
This guide walks you through the essential tools, techniques, and ethical guardrails for effective social media investigations. You'll find practical resources used by professionals in law enforcement, intelligence agencies, and corporate security worldwide.
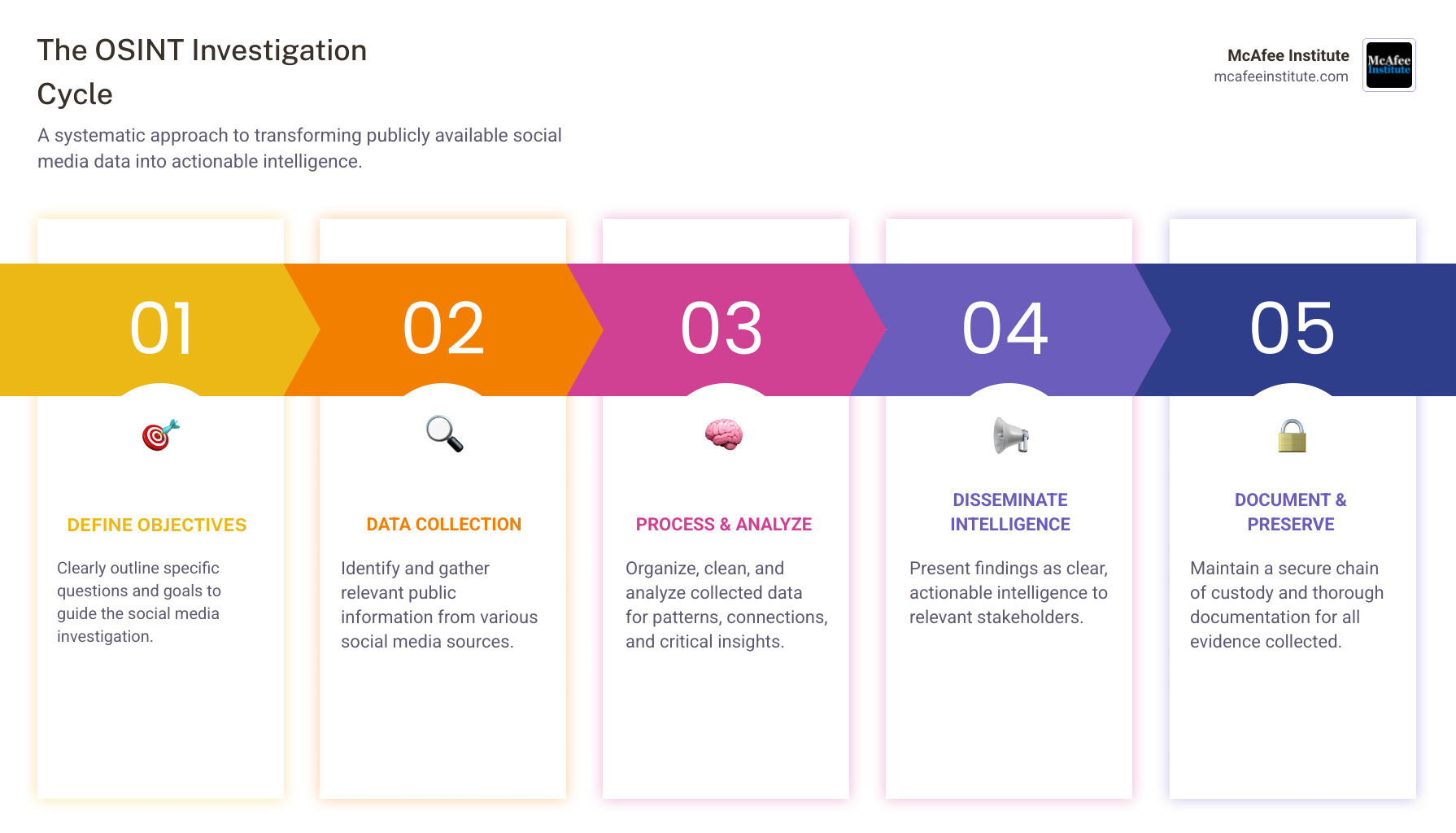
A Curated List of Open Source Intelligence Tools for Social Media
The digital landscape is vast, and knowing which open source intelligence tools for social media to deploy can save countless hours. This section breaks down powerful tools by platform and purpose.
General Purpose & Username Search Tools
When starting an investigation, you must first establish an online presence. These tools help map a subject's digital footprint.
WhatsMyName is an essential starting point. It searches for a specific username across more than 500 platforms instantly, revealing where an identity appears online. Find it at the WhatsMyName Username Tool.
For a broader view, the OSINT Framework is a comprehensive, community-driven directory of intelligence resources. It organizes hundreds of tools by category, pointing you to the right resource for your task. Explore it at The OSINT Framework.
Maltego visualizes complex connections between people, companies, domains, and other data points. It creates interactive network graphs that reveal hidden patterns and relationships.
Social Searcher monitors public social mentions across various networks in real-time. It's excellent for tracking trending topics and understanding how information spreads.
Facebook & Instagram Investigation Tools
Facebook and Instagram are treasure troves of personal information, but navigating them requires specialized tools.

Lookup-id.com finds the unique numeric ID behind a Facebook profile, page, or group. This ID is crucial for tracking accounts even if the name changes. Use it at Lookup-id.com.
Who Posted What is a powerful Facebook keyword search tool. It lets you search for keywords on specific dates, which is critical for building a timeline of events. Find it at Who posted this.
CrowdTangle Link Checker is a Chrome extension that shows where a specific link has been shared on Facebook, Instagram, Twitter, and Reddit. It helps track content propagation and identify influence networks. Install it from CrowdTangle Link Checker.
Picuki allows for anonymous browsing of public Instagram profiles, posts, and stories without logging in, which helps maintain operational security. Access it at Picuki.
SnapInsta provides a simple way to download photos, videos, and IGTV content from public Instagram accounts for offline analysis or evidence preservation. The tool is at SnapInsta.
Twitter (X) & LinkedIn Intelligence Tools
Twitter (X) is a real-time information firehose, while LinkedIn is the world's largest professional network. Both offer distinct intelligence opportunities.
TweetDeck allows you to monitor multiple Twitter timelines, hashtags, and user activities on a single screen. It's essential for tracking events in real-time. Access it at TweetDeck.
Twitter Advanced Search is a native but underused feature that lets you filter searches by keywords, accounts, dates, location, and more. Use it for highly targeted intelligence gathering at Twitter Advanced Search.
FollowerWonk offers deep insights into Twitter accounts. You can find users by their bio content, analyze their followers, and compare accounts to understand network dynamics.
RecruitEm is a great OSINT tool for LinkedIn. It uses boolean search strings to find public profiles based on criteria like job title, location, and skills. Use the tool at RecruitEm.
RocketReach helps find contact information for professionals and companies, including email addresses and phone numbers that may not be visible on a LinkedIn profile. Access it at RocketReach.
Reddit, Discord, and Forum Analysis Tools
Niche communities on these platforms offer unfiltered insights into public sentiment and group dynamics.

Reddit User Analyser visualizes the activity of a Reddit user, showing posting patterns, preferred subreddits, and engagement. Use it at Reddit User Analyser to understand online personas.
F5BOT sends real-time notifications for new Reddit posts that match specific keywords. It's excellent for monitoring topics of interest or emerging threats. Set up alerts at F5BOT.
BoardReader searches content from blogs, forums, and message boards, aggregating discussions from outside mainstream social media. Access it at BoardReader.
Discord.name helps you look up a user's profile using their Discord ID, a key step in connecting online personas across platforms. Use it at Discord.name.
These foundational open source intelligence tools for social media are a starting point. Knowing which tool to use for which task comes from practice and training.
Key Techniques for Effective Social Media Investigations
Having the right tools is only half the battle. Real skill comes from using specific techniques to transform raw data into actionable intelligence.
Mastering Search Operators and Google Dorking
Google itself is one of the most powerful open source intelligence tools for social media, but most people only scratch the surface. Google Dorking (or Google Hacking) uses advanced search commands to find specific information and filter out irrelevant results.
For example, a site-specific search like site:facebook.com "John Doe" restricts your search to Facebook. A filetype search like filetype:pdf can uncover public documents and reports. Combining operators like intitle:, inurl:, or intext: allows for laser-focused targeting of information within page titles, URLs, or body text.
These techniques let you bypass general search algorithms and dive straight into publicly indexed data that casual browsing would never reveal. For a deeper dive, explore Google Hacking (Dorks) and our guide to 5 Incredible OSINT Techniques.
Geolocation, Image, and Video Analysis
Visual content and location data can make or break an investigation. A single photo or geotagged post can place a suspect, reveal a pattern of movement, or confirm an alibi.
Many social media posts include geotagged data. Tools like Snap Map and Instahunt let you see posts from specific locations in real-time. Beyond geotags, images and videos often contain embedded EXIF data with camera details, timestamps, and sometimes GPS coordinates, which helps verify authenticity.
Reverse image search using Google Images or TinEye is another essential technique. Uploading an image can reveal where else it appears online, helping you identify its source or expose fake profiles.
For video verification, tools like InVID-WeVerify help analyze content for manipulation, check metadata, and perform reverse image searches on individual frames. This step is critical for debunking deepfakes and fabricated content.
Advanced Methods: AI, Automation, and Network Analysis
The sheer volume of social media data makes manual analysis at scale nearly impossible. This is where advanced methods become game-changers.
Artificial Intelligence and Machine Learning are revolutionizing social media intelligence. AI can perform sentiment analysis to classify emotional tone, conduct entity recognition to identify people and places in text, and analyze images to detect objects, faces, and logos. Learn more in How AI is Transforming Investigations.
Automation is critical for managing data collection. Tools can be set up to continuously extract data, send alerts for specific keywords (like with F5BOT for Reddit), or streamline workflows using platforms like IFTTT (If This Then That).
Network analysis tools like Maltego help visualize relationships between individuals and groups. By mapping likes, comments, and shares, you can identify key influencers and understand the structure of a network.
These advanced techniques amplify an investigator's judgment, but they must be used responsibly. Ethical considerations are paramount, as discussed in Ethical AI in OSINT.
Ethical and Legal Guardrails for Investigators
Using open source intelligence tools for social media brings power and responsibility. An investigator's credibility depends not just on what they find, but how they find it.
Data privacy is central to ethical OSINT. The focus must remain on publicly available information. Attempting to bypass privacy settings or use deceptive tactics to gain access crosses an ethical and often legal line. Always ask: "Does this person have a reasonable expectation of privacy here?"
Legal compliance is fundamental. Data protection regulations like GDPR and CCPA set clear boundaries. Investigators must understand and adhere to the laws in their jurisdiction, as what is legal in one country may be prohibited in another.
Each platform's Terms of Service also matter. Violating them can result in account suspension and loss of access. Many platforms prohibit automated data collection or creating fake profiles, so respecting these terms is crucial for maintaining investigative capabilities.
Data accuracy requires healthy skepticism. Information found on social media must be cross-verified from multiple independent sources. It's also vital to recognize our own biases and the biases inherent in platform algorithms.
Proper evidence handling and documentation separate professionals from amateurs. Every piece of data requires a clear chain of custody: where it came from, when it was accessed, and how it was preserved. Digital content is fleeting, so using archival tools to capture evidence is essential for it to be verifiable and legally admissible.
In short, the key ethical principles are: collect only what you need, respect legal boundaries, verify everything, document your process, and handle evidence with care. These guardrails ensure your work stands up to scrutiny.
Frequently Asked Questions about Social Media OSINT
Here are answers to common questions about the practicalities and implications of social media OSINT.
Is using OSINT tools for social media legal?
Yes, using open source intelligence tools for social media to collect publicly available information is generally legal. If information is visible to anyone without special access, it's considered open source.
However, legality depends on several factors. The intent of use is critical; using data for harassment or stalking is illegal. Circumventing security measures or privacy settings is also outside legal bounds. Furthermore, violating a platform's Terms of Service can lead to account suspension or civil liability. Finally, jurisdictional laws like GDPR vary significantly, so it's crucial to understand the regulations that apply to your specific use case.
How do I verify information found on social media?
Verification is critical in an environment rife with misinformation. A systematic approach is best:
- Cross-verification: Corroborate information from at least two independent, reliable sources.
- Source Corroboration: Analyze the poster's profile history, expertise, and track record to assess their credibility.
- Reverse Image Search: Use tools like Google Images and TinEye to check if an image is original or has been taken out of context.
- Metadata Analysis: When possible, extract EXIF data from files to verify creation dates, locations, and other technical details.
- Fact-Checking: Consult reputable fact-checking sites like Snopes or PolitiFact to verify sensational claims.
- Evaluate Context: Understand the full narrative surrounding a piece of content to avoid being misled by accurate but out-of-context information.
What are the biggest challenges in social media OSINT?
Even experienced investigators face several significant challenges:
- Data Volume: The sheer amount of data generated daily makes it difficult to find relevant intelligence without powerful tools and refined techniques.
- Disinformation: The rapid spread of false or misleading information requires constant, diligent verification.
- Privacy Settings: Evolving privacy controls and private profiles limit the scope of what can be legally and ethically collected.
- Ephemeral Content: Disappearing content, like Instagram Stories, creates preservation challenges and requires investigators to act quickly.
- Platform Evolution: Social media platforms constantly change their interfaces and APIs, meaning tools and techniques can become obsolete overnight.
- Anonymity: Pseudonyms and fake profiles make it difficult to connect online personas to real-world individuals.
These challenges are why structured education, like the Certified Social Media Intelligence Expert (CSMIE), is so valuable. It teaches the methodology needed to overcome these obstacles.
Conclusion: From Tools to Certified Expertise
The digital age has made proficiency in open source intelligence tools for social media essential. We've explored powerful tools like WhatsMyName and Maltego, and crucial techniques like Google Dorking and video verification. However, tools are just the beginning.
True expertise comes from mastering the methodologies that turn scattered data into coherent intelligence, all while navigating complex ethical and legal guardrails. The challenges of data overload, misinformation, and evolving platforms are intensifying, making continuous learning non-negotiable for professionals in this field.
At McAfee Institute, our programs are designed by experts with real-world law enforcement and intelligence experience. We focus on what works in the field.
The Certified Social Media Intelligence Expert (CSMIE) program exemplifies this approach. It provides comprehensive training on the tools, methodologies, and ethical frameworks that generate actionable intelligence. You'll gain hands-on experience and develop the critical thinking skills that separate professional analysts from amateur researchers.
What sets our certification apart? You receive lifetime access to all materials, live instructor support, and free updates for life—with no annual renewal fees. It's a one-time investment in your continuous professional development.
Investing in a professional certification positions you as a trusted expert in a critical field. Whether you're in law enforcement, corporate security, or intelligence analysis, these skills open doors to new opportunities.
Ready to advance your career? We invite you to explore all board certifications and find the program that aligns with your professional goals. With the right training, you'll be equipped to master the evolving digital landscape.











Share:
Spotting Shadows Machine Learning's Edge in Cybersecurity
Beyond the Shadows: The Path to a CIA Intelligence Career