
Learn the A-Z's of Cyber Counterintelligence

Learn the A-Z's of Cyber Counterintelligence
Certificate Earned
Digital Certificate of Completion & 1 CPE Credits
Duration
2 hours of structured video tutorials, interactive quizzes, practical labs, and applied research assignments.
Delivery
Fully online, self-paced learning—accessible anytime, anywhere, designed for flexibility in any schedule.
Guarantee
3-Day Money-Back Guarantee and Lifetime Access—try the course risk-free and enjoy lifetime updates.
Program Overview
Program Topics
Explore the Program Curriclum Below
Eligbility Requirements
Top organizations offer this certification to their employees.
This certification was selected for our collection of top-rated credentials, trusted by government, military, and law enforcement agencies worldwide for its rigor, relevance, and practical application. Backed by recognized standards and comprehensive support, it empowers professionals to excel and drive impactful results.
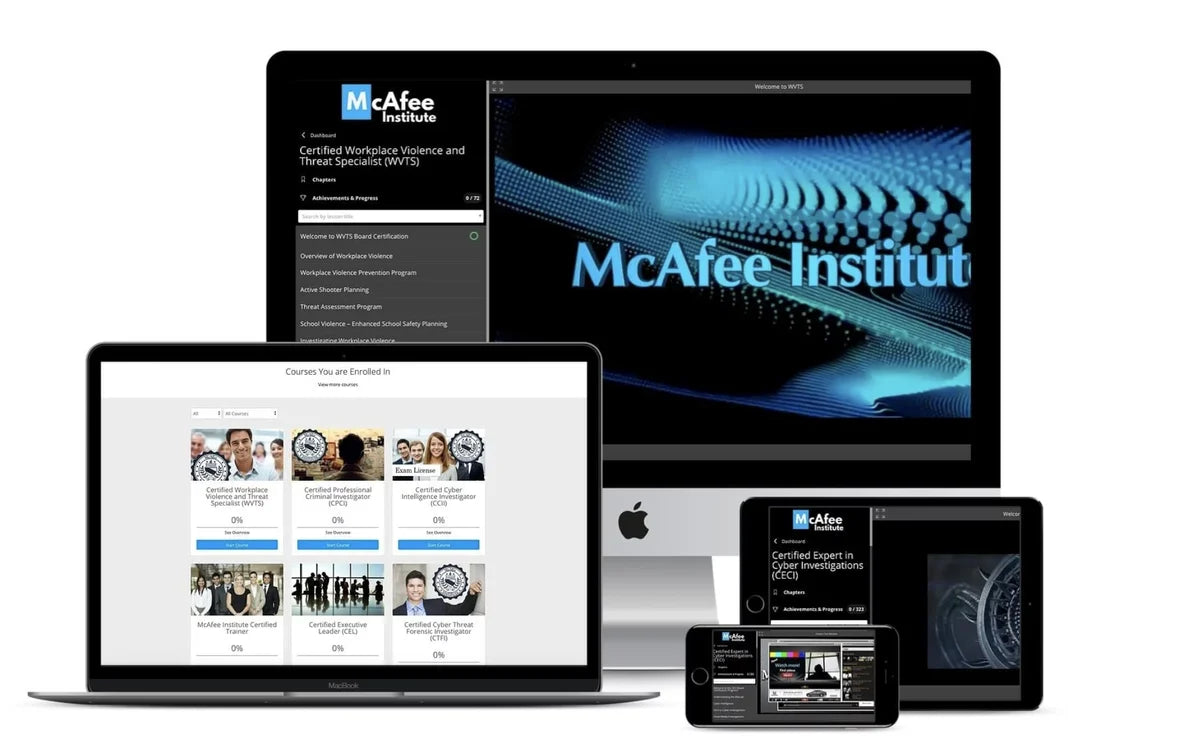
A Dynamic Learning Environment Built for Your Success
Engage in hands-on, real-world learning through our platform’s intuitive design, built for easy navigation and optimized for lifelong learning. Our user-friendly platform offers everything you need to master critical skills—from in-depth course materials and live instructor support to self-paced quizzes and lifetime access.
If you have any questions, you are always welcome to contact us. We'll get back to you as soon as possible, within 24 hours on weekdays.
-
Shipping Information
Use this text to answer questions in as much detail as possible for your customers.
-
Customer Support
Use this text to answer questions in as much detail as possible for your customers.
-
FAQ’s
Use this text to answer questions in as much detail as possible for your customers.
-
Contact Us
Use this text to answer questions in as much detail as possible for your customers.






